The Covid-19 outbreak, hereinafter 'coronavirus', requires flexibility and perseverance on the part of both companies and their employees. From the point of view of curbing the further spread of the virus, teleworking is being used en masse.
Desks were quickly installed in every home or bedroom, extra screens were installed and online services (Teams, Skype,...) were subjected to a rigorous stress test. The coronavirus and the rise of teleworking go hand in hand in many countries.
A completely new, somewhat bizarre situation, which also gives rise to great things, such as solidarity and support for all the healthcare providers who protect us day in and day out.
Unfortunately, however, it is also being abused. After all, cyber criminals do not sit still and try to make the most of the many teleworkers. Various techniques and methods are used to obtain passwords or find weak spots in the security of companies.
Phishing: the modus operandi
Phishing is once again numerous. E-mails or text messages contain malicious attachments or suspicious links, but malware, fake websites and apps are also used to lure the unsuspecting teleworker into a trap. And this on the basis of one common theme, the coronavirus, hence the introduction of the term 'corona-phishing'.
Cybercriminals will in practice, just as with general phishing mails, present themselves as a reliable authority or organization. However, the coronavirus leads to phishing attacks increasingly responding to fear and insecurity.
Various agencies, such as the police and the Centre for Cybersecurity, therefore warn against e-mails or messages that appear to come from healthcare providers, banks or organisations that provide information about the coronavirus. Some techniques for which the teleworker must be vigilant are explained below.
Phishing: the techniques
The simplest technique is initially not directly related to the coronavirus, but corresponds to teleworking. Cybercriminals will approach teleworkers from the 'IT helpdesk' scenario, calling employees to inform them about a so-called 'IT problem', but in reality trying to extract their data.
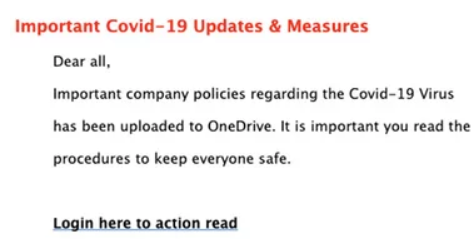
In turn, some techniques are specifically linked to the coronavirus. Below you can find a screenshot related to a OneDrive login page. In this scenario, cyber criminals will present themselves as your manager or partner, with the request to read the new coronavirus business procedures. The e-mail contains a fake link to OneDrive's login page in order to get your login details and password.
There are also phishing mails circulating, containing, for example, various symptoms of the coronavirus and a PDF file attached, with safety measures to protect against the virus. In reality, when opening the attachment, malware (such as ransomware) will be placed on your computer, with all its consequences.
Attachments that accurately reflect the latest evolutions of the coronavirus are also to be mistrusted. Some phishing mails even mention, for example, the name of Johns Hopkins University, which, for the sake of clarity, actually exists and is actually researching the coronavirus. The layout is authentically imitated, but in reality these attachments contain a virus.
Some tips to avoid phishing
There may be fatigue, stress, but mainly distractions and lack of concentration during this period, for example due to the combination of teleworking and the children walking around the house energetically. In other words, a mistake can be made very quickly.
Nevertheless, teleworking should not automatically lead to reduced alertness! With clear agreements and the correct preventive measures, teleworking can also mean a safe working environment.
First of all, pay attention to installing various tools or switching on programs or online applications that you have not used before. Contact your IT environment or the responsible persons within your company as much as possible.
If there are e-mails or text messages about the coronavirus, stay critical and do not just click on links or attachments. If in doubt, always contact your IT environment or the sender in question.
If you did click on a link or attachment, always notify your IT environment so that they can take the necessary measures to deal with the situation further.
Any further questions or need for extra phishing and security awareness? Don't hesitate to contact our Data Security business line!
Stay safe!



